Hackers are constantly evolving their tactics to outsmart even the savviest internet users. One of their sneakiest tricks? Using lookalike URLs that seem legitimate at first glance but can lead you straight into a trap. Let’s dive into this growing Cybersecurity threat, explore how it works, and arm you with practical tips to stay safe online.
What Are Lookalike URLs?
Lookalike URLs, also known as homograph attacks, are malicious web addresses designed to mimic legitimate ones. Hackers exploit the visual similarity between certain characters to create URLs that appear trustworthy but direct you to phishing sites, malware downloads, or other dangerous destinations.
For example, imagine you receive an email with a link to “www.apple.com.” At a quick glance, it looks like the real deal. But upon closer inspection, the “a” in “apple” might actually be the Cyrillic character “а” (U+0430), which looks identical to the Latin “a” (U+0061) in most fonts. This tiny difference can redirect you to a fake site designed to steal your login credentials, financial information, or personal data.
How Do Hackers Pull This Off?
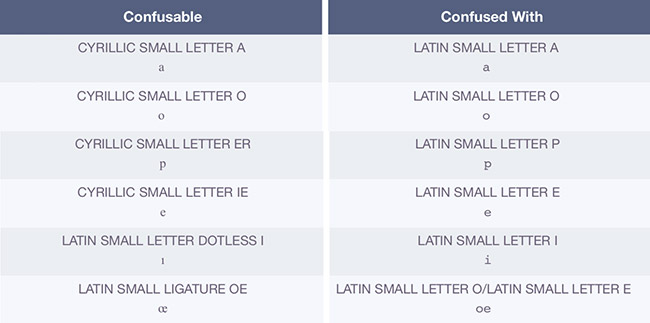
The trick lies in the Unicode system, which supports characters from various writing systems, including Latin, Cyrillic, Greek, and more. Many of these characters look nearly indistinguishable to the human eye. For instance:
Latin “a” (U+0061) vs. Cyrillic “а” (U+0430)
Latin “o” (U+006F) vs. Cyrillic “о” (U+043E)
Latin “e” (U+0065) vs. Greek “е” (U+03B5)
Hackers register domains using these lookalike characters, creating URLs that are visually convincing but entirely unrelated to the legitimate site. For example, a fake “www.paypal.com” might use a Cyrillic “р” instead of the Latin “p,” leading you to a phishing page that looks like PayPal’s login screen but is designed to capture your credentials.
Why Is This So Dangerous?
A single character can be the difference between a secure website and a full-blown security breach. Once you land on a malicious site, you might:
- Lose sensitive data: Phishing sites often trick users into entering usernames, passwords, or credit card details.
- Download malware: Clicking a link could trigger an automatic download of malicious software that compromises your device.
- Fall for scams: Fake websites might impersonate banks, retailers, or other trusted entities to steal your money or personal information.
These attacks are particularly effective because they exploit human psychology. We’re conditioned to skim URLs, especially in familiar-looking emails or messages, and most of us don’t inspect every character closely.
Real-World Examples
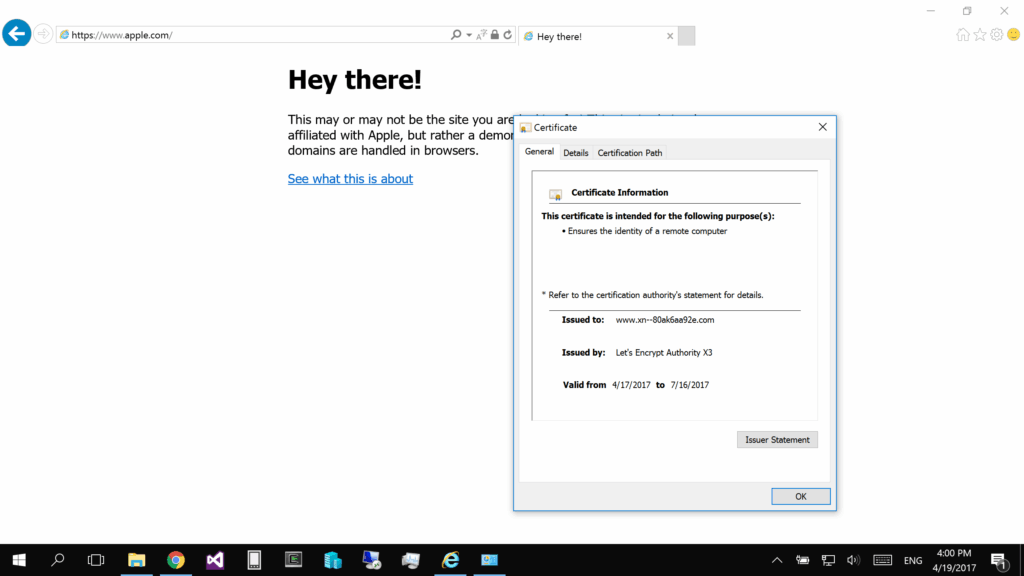
Homograph attacks have been around for years but are becoming more sophisticated. In 2017, security researcher Xudong Zheng demonstrated this vulnerability by registering a domain using Cyrillic characters to mimic “apple.com.”
Browsers displayed the URL as visually identical to the real Apple website, tricking users into believing it was legitimate. Since then, hackers have used similar tactics to impersonate banks, social media platforms, and e-commerce sites.
How to Protect Yourself
Staying safe from lookalike URLs requires vigilance and a few simple habits. Here’s your cybersecurity toolkit:
1. Inspect URLs Carefully
Before clicking any link—especially in emails, text messages, or social media—hover over it to reveal the full URL. Look for anything suspicious, like unusual characters or slight misspellings. If the URL looks off, don’t click.
Related: How to inspect a complete website URL address
2. Check the Domain Directly
Instead of clicking a link, manually type the website’s address into your browser. For example, if you get an email from “your bank,” go directly to the bank’s official website by typing the URL you know is correct.
3. Use a Modern Web Browser
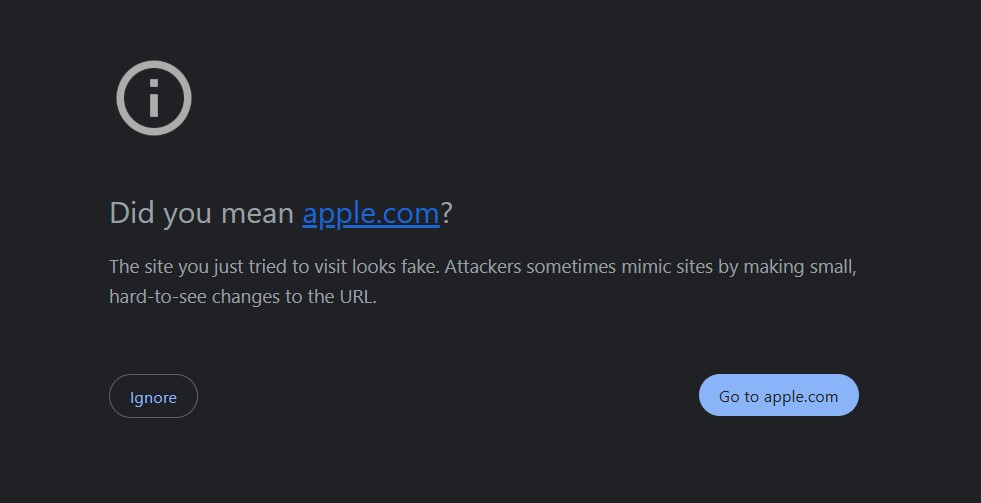
Most modern browsers, like Google Chrome, Firefox, and Safari, have built-in protections against homograph attacks. They may display a warning or convert suspicious URLs to their “punycode” form (e.g., xn--80ak6aa92e.com) to reveal the use of non-Latin characters. Keep your browser updated to benefit from the latest security features.
4. Enable Two-Factor Authentication (2FA)
If a hacker does manage to steal your login credentials, 2FA adds an extra layer of protection by requiring a second form of verification, like a code sent to your phone.
5. Be Wary of Emails and Messages
Phishing emails are a common way to distribute lookalike URLs. If an email urges you to click a link urgently (e.g., “Your account is locked!”), be skeptical. Verify the sender’s email address and contact the organization directly if you’re unsure.
Related: How to protect your domain from spoofing and email SPAM
6. Use a Password Manager
Password managers often include features that detect and warn you about suspicious URLs. They can also help you avoid typing credentials into fake login pages.
A Final Word
Hackers are getting smarter, but with a little caution, you can stay one step ahead. Lookalike URLs are a clever trick, but they rely on you overlooking the details. By slowing down, inspecting links, and practicing good cybersecurity habits, you can protect yourself from falling into their traps.
Pro Tip: Always double-check URLs, especially in emails. One wrong click could lead to a world of trouble. Stay vigilant, stay safe!
