An insecure WordPress installation can lead to a variety of risks, including data breaches, malware infections, website defacement, loss of user information, damage to reputation, SEO issues, and even potential legal consequences.
These vulnerabilities often arise from outdated installations, weak passwords, unpatched plugins, and poor security practices. Hackers can exploit these weaknesses to gain unauthorized access to your website and manipulate its content or functionality.
In this guide, we will discuss basic security measures that can help you protect your WordPress dashboard and prevent unauthorized access. By taking these steps now, you can significantly improve your website’s security and reduce the risk of cyber threats.
1. Publish Only Under Contributor Accounts
One of the ways attackers discover your administrator username is by scanning the author links on your WordPress site. Each author’s username is visible in the URL (e.g., wordpress.com/author/yourusername). If you’re using an account with administrator privileges to author articles, a hacker only now needs to guess the password to gain full control of your site.
To reduce this risk, consider creating Contributor accounts for all users who need to submit posts. Under a Contributor account, a user can only draft posts and cannot publish or delete them. This way, even if a hacker gains access to an account, they won’t be able to perform any administrative actions.
Create a Secret Administrator Account
While Contributor accounts are useful for publishing content, you can still perform all your editorial and publishing tasks from an administrator account. The trick is to change the author to a Contributor before you publish the post. This ensures that your administrator username is never exposed publicly.
The secret administrator account should have a strong, unique username and password. For the username, use at least 16 random characters, including letters, numbers, and an underscore. The password should be equally strong, with a mix of letters, numbers, and special characters.

Keep It Secret
The secret administrator account should never be referenced publicly. Any links containing the admin username or user ID could be found by web crawlers.
To ensure maximum security, all posts and pages should be authored by Contributor accounts. Additionally, you can monitor attempts to access your administrator account by using a plugin that keeps a record of login attempts (more on this later).
2. Disable XML-RPC
XML-RPC is a feature in WordPress that allows external services to interact with your website. However, it can be exploited by hackers for attacks, such as Distributed Denial of Service (DDoS) and brute force attempts. To safeguard your site, it’s important to disable vulnerable XML-RPC methods.
One effective way to enhance your site’s security is by using the Disable XML-RPC Pingback plugin. This plugin selectively disables methods in XML-RPC that are most commonly targeted by attackers, while still allowing necessary functionality for plugins and mobile apps that rely on XML-RPC, such as certain Jetpack modules.
If you don’t use XML-RPC or any related features, you can completely disable it by editing your functions.php or .htaccess file. Doing so removes the potential for abuse and adds an extra layer of protection against unauthorized access.
PHP
add_filter( 'xmlrpc_enabled', '__return_false' );
.htaccess
# Block WordPress xmlrpc.php requests <Files xmlrpc.php> order deny,allow deny from all allow from xxx.xxx.xxx.xxx </Files>
3. Install Loginizer
Loginizer is a WordPress plugin designed to protect your site from brute force attacks by blocking login attempts from an IP address after a certain number of failed attempts. This plugin helps secure the core of your WordPress site with several features, such as brute force protection, two-factor authentication (2FA), CAPTCHA, MD5 checksum, and more.
Once you have Loginizer installed, you should configure it to maximize its effectiveness:
- Set retry attempts to 2: This limits the number of failed login attempts to just 2 before the system locks out the IP address. This helps prevent attackers from trying to guess your password.
- Extend lockout time: Increase the lockout time to at least an hour or more. This discourages repeated brute force attempts by making it more difficult for attackers to continue trying.
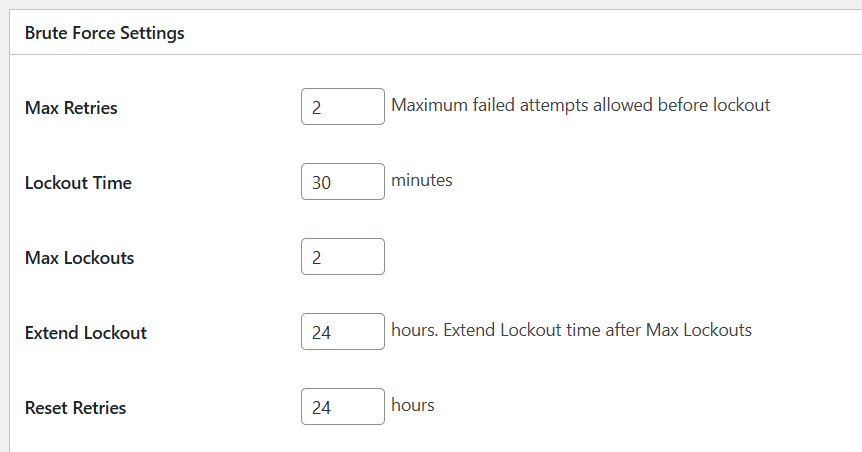
Be cautious when setting up these configurations, as they will lock you out of your WordPress site if you enter your username and password incorrectly too many times. It’s a good practice to test your login information before making these changes to avoid being accidentally locked out.
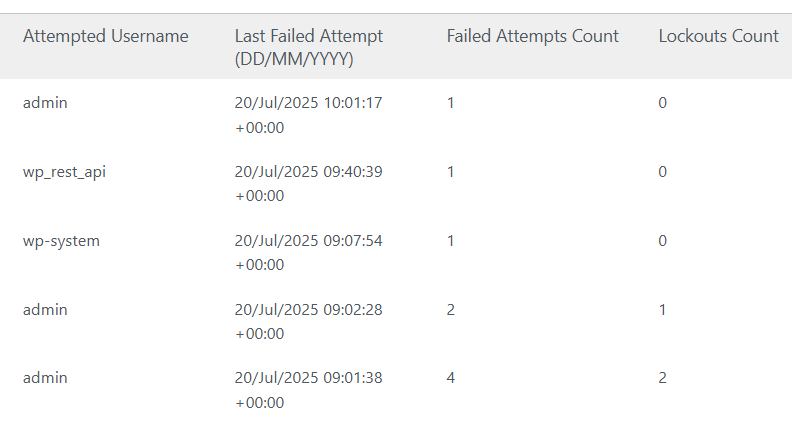
4. Monitor Your Logs
Regularly monitoring your system logs is an important step in securing your WordPress site. By checking the logs, you can track login attempts, especially those made using specific usernames.
If you notice any attempts to log in with your secret (or “ghost”) administrator account, it’s a sign that the account may have been leaked. In this case, you should create a new administrator account with a stronger, more secure username and password.
If the issue persists and you continue to see login attempts with the compromised admin account, it’s crucial to investigate the source of the leak. This may involve checking your plugins, themes, or any third-party services that may have exposed your credentials.
Regular log monitoring helps catch potential security breaches early, allowing you to take action before any significant damage is done.
Conclusion
Securing your WordPress site from brute force attacks and other potential vulnerabilities is important for maintaining its integrity and protecting sensitive data. By following the steps outlined in this guide—such as publishing only under Contributor accounts, creating a secret administrator account, installing security plugins like Loginizer, disabling XML-RPC, and monitoring your system logs—you can greatly enhance your site’s defense against cyber threats.
These strategies help reduce the risk of unauthorized access, prevent common attack methods, and ensure that your website remains secure. Regular monitoring and proactive security measures are key to keeping your WordPress site safe from evolving threats.
You May Also Like
- Advanced PHP Techniques for Hacking Yoast Metadata in WordPress
- Secure Your Network: How to Set Up OpenVPN on Linux (CentOS/Ubuntu/Debian/Amazon)
- Secure File Transfer: Which Type of FTP is Best?
- Enabling TLS 1.3 in NGINX on CWP/CentOS 7/8/EL7/EL8
- Don’t use stock images until you understand these important copyright basics
